A high-risk vulnerability (CVE-2020-13699) in TeamViewer for Windows could be exploited by remote attackers to crack users’ password and, consequently, lead to further system exploitation.

About TeamViewer
TeamViewer is an application developed by German company TeamViewer GmbH and is available for Windows, macOS, Linux, Chrome OS, iOS, Android, Windows RT Windows Phone 8 and BlackBerry operating systems.
It is used primarily for remote access to and control of various types of computer systems and mobile devices, but also offers collaboration and presentation features (e.g., desktop sharing, web conferencing, file transfer, etc.)
Since the advent of COVID-19, enterprise use of the software has increased due to many employees being forced to work from home.
Is Teamviewer worth the risk?
We have always appreciated Team Viewers capabilities but do not recommend using the full installed version. The ONLY version of Teamviewer that we think should be used in a business or IT Service company is the “Run Only” version or “Join Only” one time use versions that you download and approve to use and it uninstalls after the session.
Why not use Teamviewer?
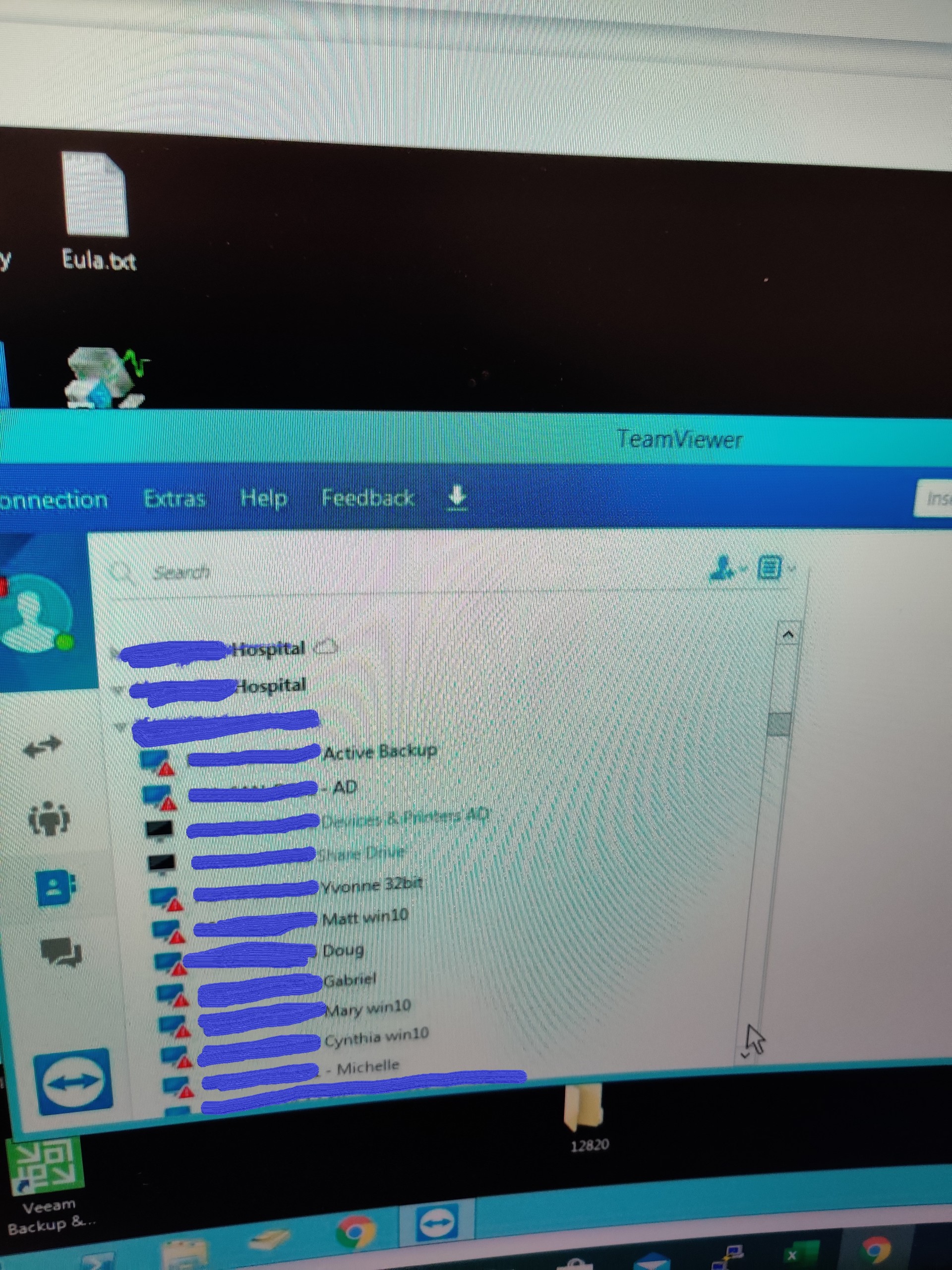
This week before the exploit announcement was known to use we were in the process of taking over an account from a larger local MSP in San Antonio that apparently used Teamviewer exclusively and we were able to not only see the customers information, but EVERY customer of that MSP was exposed to us from inside this 1 customers server?? We were able to see and access if we wanted to (we did not) all PC’s, servers, etc that had teamviewer installed were exposed and if we were a bad actor we would have been able to easily exploit every customer with any type of ransomware we wished. See the pic below I took with my cell phone to send to the MSP. (names removed for security) but the 1st on the list was a hospital in the middle of COVID-19 is exposed. There were also MANY MANY Dentists, Veterinarians, involved in this as well. Prime Ransomware candidates.

removed the names to protect
We notified the MSP and are monitoring the situation. If they do not clean up their act we will notify the customers of the breach in security and offer free help in resolving it.
Our Take:
Do not install team-viewer on your machine for full time access and be wary of any IT person on company that uses Teamviewer as their remote access tool.
For more on the vulnerability visit the site https://www.helpnetsecurity.com/2020/08/06/cve-2020-13699/

Leave A Comment